
The ever-changing nature of modern technology means that nearly every human on the planet has access to interconnected systems at their fingertips, every day. However, the complexity of software and the diversity of embedded firmware means that securing these systems is a constant, evolving challenge.
The threat of computer misuse is growing and pervasive. In 2023, the UK National Cyber Security Centre received a record number of threat reports – increasing 64% year-on-year from 1,226 to 2,005. Moreover, the impact of disruption to devices was put into stark reality by the recent Microsoft outage caused by an update deployed by CrowdStrike, a cyber security company.
Encrypting data can be a defensive measure against cyber threats. But the ease of access to encryption algorithms and secure software can also be leveraged by malicious actors. In recent history, EncroChat became a prolific tool for organised crime networks to plan criminal activities in secret through encrypted messages sent via modified smartphones.
However, in 2020 the National Crime Agency (NCA) along with other international law enforcement agencies used specialist data exploitation capabilities to analyse thousands of messages leading to the arrest of close to 1,000 criminals as well as the seizure of millions of pounds worth of contraband.
The challenge is therefore twofold: how do we secure the systems upon which society is reliant for prosperity and legitimate commercial activity, while being able to find flaws in and gain access to the communication devices exploited by criminal actors?
Vulnerability research
Vulnerability research (VR) identifies flaws and weaknesses in software, firmware and hardware to reduce the risk of comprise to intended purpose. VR tools and investigation processes have advanced considerably over recent years, with software becoming more productive than ever. However, a fundamental constraint remains: VR scales only by the number of people applied to the problem.
As with any developing technology, VR talent is scarce. Industry capability is limited to the capacity of suitably qualified and experienced personnel. Advances in AI have transformed the speed of developing new capability at scale. So, the real question is how to blend technology with human judgement to verify the outcomes delivered to keep pace with the speed of new developments? The security of an AI-powered world requires scaled use of VR using methods less dependent on human capital.
Roke is at the forefront of efforts to resolve this challenge. Our unique combination of expertise and proprietary tooling provides our clients with an advanced, highly scalable VR solution.
Augmenting researchers
One of our key strategies is to augment the actions of human operators with machines. This scales VR efforts using computing power in tandem with people power.
Critically, this is not about replacing researchers; it’s about supplying them with new tools that help them perform their job across multiple projects. Technology offers an opportunity to reduce toil – i.e., automating ‘monotonous’, ‘handle-turning’ work to allow researchers to spend more time on novel, more complex tasks requiring human cognition, intuition and creativity.
That said, it’s crucial to avoid using automation or machine learning for its own sake. To provide operational value, our focus is on understanding the value that automation can add to specific tasks within the overall VR process.
Automating for success
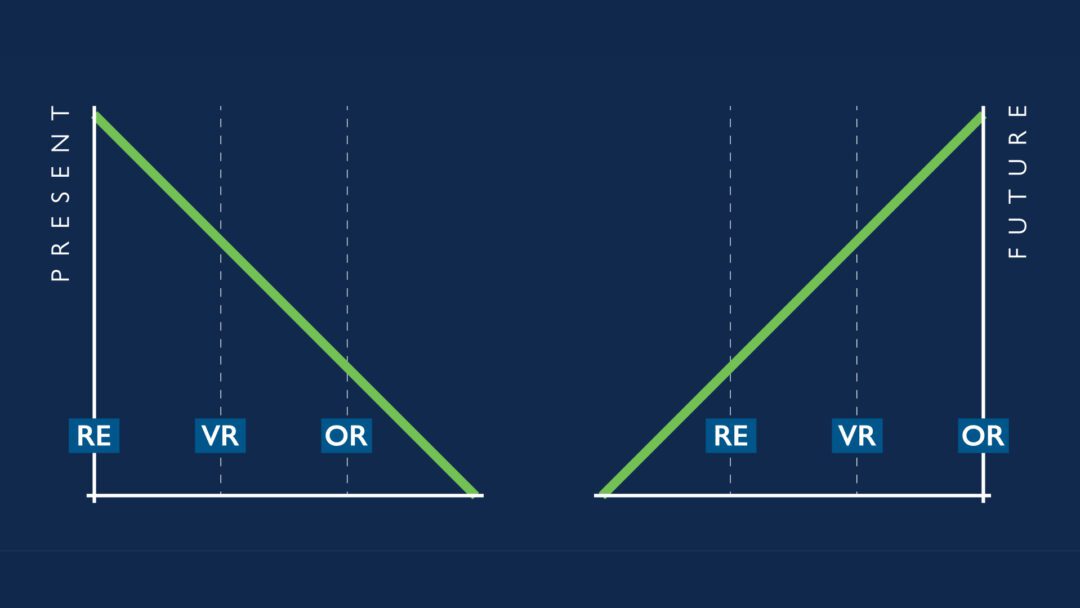
Currently, skills and experience within this area are divided among Reverse Engineering (RE), VR and Operational Research (OR). This is indicated in the graphic (bottom left). Where there is a good amount of talent able to work on RE tasking, there are fewer that can work on VR tasking, and in turn, even fewer that can work on OR tasking. Our vision for automation is a world that looks more like the latter image (bottom right). Here, researchers can focus their time on interesting OR and VR problems because the monotonous RE, VR, and OR tasks have been automated for them.

How are we applying this to client problems?
Our National Security team directs its VR activity on providing both UK and partners with the capability to accelerate and enhance vulnerability research practices. We do this by focusing on three main areas to provide solutions to our customers:
- Direct VR contract engineering supported by tooling
- Licensing of VR automation and machine learning products
- Working on customer funded research to accelerate VR related use-cases
One of our automated VR tools is a ‘fuzzing at scale’ framework. Fuzzing is an automated software testing technique that involves providing invalid, unexpected, or random data as inputs to a computer program. Roke’s approach is designed to accelerate and reduce the manual effort behind fuzzing and triaging the resulting outcomes at scale. Critically, this framework allows researchers to focus on the key VR work that require a human’s touch, while enabling fuzzing and triage to scale using compute rather than people.
Separately, we have developed Strix. This is an automated target analysis tool, ingesting firmware and binaries and running automated analysis modules to identify vulnerabilities, misconfigurations, and weaknesses both dynamically and statically. This uses a combination of in-house machine learning models and automated analysis techniques. After the analyses are complete, the tooling provides a low volume, impactful report providing researchers with recommendations on where further analysis may help with their tasking.
By using both tools, Roke teams have demonstrated the capability of automated VR to identify vulnerabilities in targets of interest more quickly and at lower cost than traditional manual methods. This force multiplier effect of this approach is critical to clients who are faced with resource and time pressures to achieve success.
Hear from an expert
Earlier this year, one of our Consultant Engineers, James delivered a talk to B-Sides Cheltenham on Automating Binary Analysis with Machine Learning which explains how automation tooling in areas such as VR can help researchers, provide quick wins and fix problems. Watch now:

Get in touch
Careful use of AI, automation and human judgement is transforming our world. Contact us now to find out how Roke’s approach to VR can help your organisation.
Conclusion
By automating vulnerability research with AI-powered fuzzing frameworks and Strix analysis, Roke accelerates discovery and triage—freeing skilled researchers to focus on critical threats, delivering faster, more cost-effective defenses, and enabling defence and security teams to strike before adversaries can exploit weaknesses.


